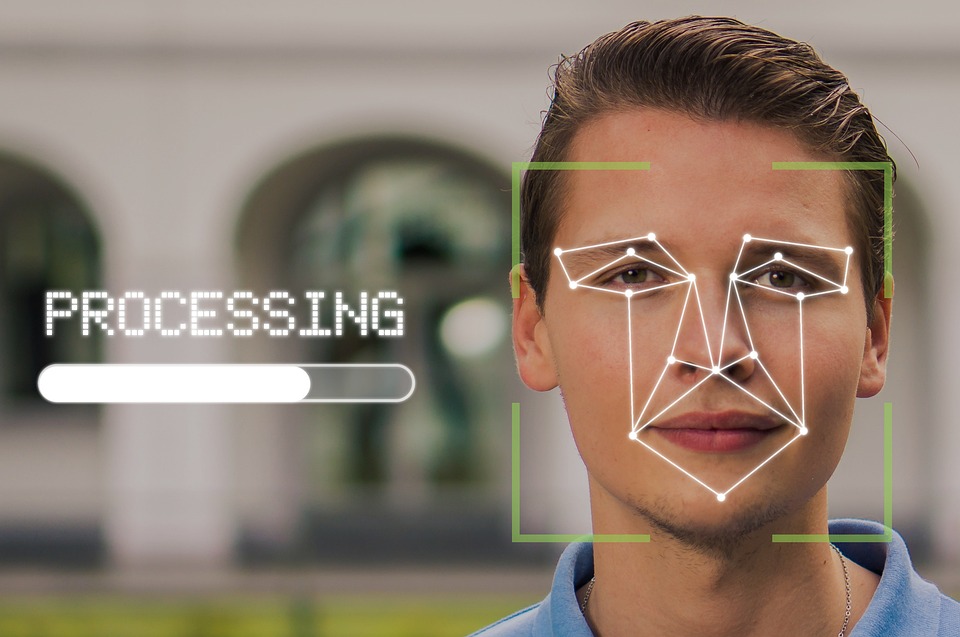
In an increasingly digital world where traditional password-based authentication methods are prone to security breaches and user inconvenience, biometric authentication offers a compelling solution. By leveraging unique biological traits such as fingerprints, facial features, iris patterns, and voiceprints, biometric authentication provides a secure and user-friendly way to verify identity.
This article explores the principles, applications, and implications of biometric authentication in the realms of security, privacy, and user experience.
Understanding Biometric Authentication:
Biometric authentication is a technology that relies on biological characteristics to authenticate individuals. Unlike traditional authentication methods such as passwords or tokens, which can be lost, stolen, or forgotten, biometric traits are inherently tied to an individual’s identity and are difficult to replicate or spoof.
Biometric authentication systems capture biometric data from users, process it using algorithms to extract distinctive features, and compare it against stored templates to verify identity.
Types of Biometric Modalities:
Biometric authentication encompasses a variety of modalities, each with its strengths, limitations, and applications:
- Fingerprint Recognition: Fingerprint biometrics is one of the most widely used modalities, leveraging the unique patterns of ridges and valleys on an individual’s fingertips for identity verification.
- Facial Recognition: Facial biometrics analyzes the unique facial features of individuals, such as the arrangement of eyes, nose, and mouth, to verify identity.
- Iris Recognition: Iris biometrics measures the unique patterns in the colored part of the eye (iris) to authenticate individuals with high accuracy.
- Voice Recognition: Voice biometrics analyzes the unique characteristics of an individual’s voice, including pitch, tone, and cadence, for identity verification.
- Palmprint Recognition: Palmprint biometrics captures the unique patterns on the palm of an individual’s hand for authentication purposes.
- Behavioral Biometrics: Behavioral biometrics analyzes patterns of behavior, such as typing rhythm, gait, and signature dynamics, to authenticate users.
Applications of Biometric Authentication:
Biometric authentication finds applications across a wide range of industries and use cases:
- Mobile Devices: Many smartphones and tablets integrate biometric authentication features, such as fingerprint scanners and facial recognition, to unlock devices and authorize transactions securely.
- Financial Services: Banks and financial institutions use biometric authentication to enhance the security of online banking, payment transactions, and ATM access.
- Border Control and Immigration: Biometric technologies are deployed at border checkpoints and immigration control points to verify the identity of travelers and enhance border security.
- Physical Access Control: Biometric authentication is used to control access to secure facilities, buildings, and restricted areas, replacing traditional keys or access cards.
- Healthcare: Biometric authentication ensures secure access to electronic health records (EHRs), medical devices, and patient information in healthcare settings.
- Law Enforcement: Law enforcement agencies use biometric technologies for forensic identification, suspect verification, and criminal investigations.
Challenges and Considerations:
While biometric authentication offers significant advantages in terms of security and user experience, it also presents challenges and considerations:
- Privacy Concerns: Biometric data is highly sensitive and requires robust privacy safeguards to prevent unauthorized access, misuse, or exploitation.
- Security Risks: Biometric systems are not immune to attacks, and vulnerabilities such as spoofing, replay attacks, and database breaches must be mitigated through robust security measures.
- Interoperability: Ensuring interoperability and compatibility across different biometric systems and devices is essential for seamless integration and user adoption.
- Ethical and Legal Implications: Biometric technologies raise ethical and legal questions related to consent, data ownership, and surveillance, requiring careful consideration and regulatory oversight.
Biometric authentication represents a paradigm shift in identity verification, offering a secure, convenient, and reliable alternative to traditional authentication methods.
As biometric technologies continue to advance and evolve, they hold the potential to transform how we authenticate users, access services, and interact with technology in a wide range of contexts.
By addressing challenges related to privacy, security, and ethical considerations, biometric authentication can pave the way for a future where identity verification is seamless, ubiquitous, and trustworthy.
Identity verification is a critical component of security and trust in various domains, including financial services, healthcare, e-commerce, and government. As digital interactions become increasingly prevalent, the need for secure and seamless identity verification methods is more pressing than ever. This article explores the future of identity verification, focusing on emerging technologies, innovative approaches, and trends shaping the landscape.
Biometric Authentication: Beyond Fingerprint Recognition
Facial Recognition
Facial recognition technology has gained significant traction in recent years, offering a convenient and secure means of identity verification. Advancements in machine learning algorithms have improved facial recognition accuracy and robustness, enabling widespread adoption in smartphones, airports, and banking applications.
Iris Scanning
Iris scanning technology provides a highly secure form of biometric authentication by capturing unique patterns in the iris of the eye. Iris scans offer a high level of accuracy and are difficult to spoof, making them ideal for applications requiring strong authentication, such as border control and access to high-security facilities.
Voice Recognition
Voice recognition technology analyzes unique characteristics of an individual’s voice, such as pitch, tone, and cadence, to verify their identity. Voice biometrics offer a convenient and natural means of authentication, particularly for phone-based transactions and customer service interactions.
Multi-Factor Authentication: Strengthening Security
Behavioral Biometrics
Behavioral biometrics analyze patterns of user behavior, such as typing speed, mouse movements, and touchscreen interactions, to authenticate users. Behavioral biometrics offer continuous authentication capabilities, detecting anomalies and unauthorized access attempts in real-time.
Contextual Authentication
Contextual authentication factors consider environmental variables, such as device location, network connection, and time of day, to assess the risk level of a login attempt. By analyzing contextual data, authentication systems can adapt security measures dynamically to match the perceived risk level.
Blockchain-Based Identity Solutions: Decentralized and Trustworthy
Self-Sovereign Identity
Self-sovereign identity solutions leverage blockchain technology to enable individuals to control and manage their digital identities securely. By decentralizing identity data and providing cryptographic proof of identity, self-sovereign identity solutions offer greater privacy, security, and user autonomy.
Decentralized Identifiers (DIDs)
Decentralized Identifiers (DIDs) are a foundational component of self-sovereign identity systems, providing globally unique identifiers for individuals, organizations, and devices. DIDs are designed to be cryptographically verifiable, privacy-preserving, and interoperable across different identity platforms and applications.
Future Trends and Considerations
Biometric Fusion
Biometric fusion combines multiple biometric modalities, such as fingerprint, facial, and voice recognition, to enhance authentication accuracy and resilience. By leveraging multiple biometric factors, fusion techniques can mitigate the limitations and vulnerabilities of individual biometric modalities.
Continuous Authentication
Continuous authentication mechanisms monitor user behavior and biometric indicators throughout the duration of a session, rather than relying on a single authentication event. Continuous authentication enhances security by detecting and responding to changes in user behavior or environmental conditions in real-time.
Privacy-Preserving Technologies
Privacy-preserving technologies, such as zero-knowledge proofs and homomorphic encryption, enable secure authentication and identity verification without exposing sensitive user data. By preserving user privacy and confidentiality, these technologies address growing concerns about data breaches and identity theft.
The future of identity verification is characterized by a convergence of biometric authentication, multi-factor authentication, and blockchain-based identity solutions. As technology continues to evolve, identity verification methods will become more secure, seamless, and privacy-preserving, enabling trusted interactions in an increasingly digital world.
By embracing innovative approaches and staying ahead of emerging threats, organizations can ensure the integrity and reliability of their identity verification processes, fostering trust and confidence among users and stakeholders alike.